Hello everyone and I welcome you to a very interesting ICT blog. We all are plugged into the internet one way or the other and by default, we all can communicate with each other but I would love to ask us this little question, when was the last time you came in contact with IP address or a domain name server? Do we even know the DNS of the network we are using? One good thing about technology is that it is here to ease our troubles (for the people at the front end).

[Credit: Wikimedia. Creative Commons Attribution-Share Alike 2.5 Generic license. Author: cawi2001]
The first personal gadget I had that could use the internet was my Nokia express music phone which I got in 2008. I counted myself lucky since the major service provider in my country (MTN) was testing there internet facilities, hence once you're technical enough to figure out their IP address and other "gibberish" needed to connect to the internet, you're good to go. There was nothing like data subscription then and there was also nothing like automatic configuration or push configuration then but I was exposed enough to the "ingredients" needed for network connections but I must say that it was hell tracking the changes in their IP address and other configuration information.
Today, the story is no longer the same as we only bother about data subscription and no one is talking about connection problems once you have an active data subscription. But why is that? Did our gadgets get smarter? The answer to that is both yes and no, yes our gadgets got smarter and no because a protocol was designed to take care of host network configuration.
The dynamic host configuration protocol
DHCP is a protocol that allows network users, administrators and even gadgets to automatically assign and obtain network connection details. DHCP is a modified version of BOOTP (bootstrap protocol), hence, they have a lot in common. While the DHCP provides a plug and play services to any "eligible" user in a network, BOOTP provides easy configuration between workstations and servers. Therefore the BOOTP provides both automatic network configuration and IPL (initial program load source) while DHCP provides only network configurations.
DHCP operations
When we newly enter an organization, it is very much likely that we won't know the complete organizational structure. The same is applicable to devices that you just introduced into the network. Every device needs an IP address, a subnet mask which gives a complete meaning to the IP address, a domain name system address, a gate way address, etc. Unless you're the network administrator, it is impossible to provide these information and even if you can, it would be a tedious and confusing job.
))
[Windows is capable of both automatic and dynamic address allocations. A screen shot from my PC
DHCP uses three mechanisms for providing configuration parameters to incoming users of a network, these mechanisms are automatic allocation, manual allocation and dynamic allocation mechanism. Each of these mechanism uses a client-server model. In the client-server model, the server is also a network host tasked with listening for incoming request from any other device seeking for configuration information. In the case of using our phones for hotspots, our phone is the DHCP server while the device (it could be our laptops or other phones) requesting for connectivity is the client. Hence, the server does not necessarily mean a stationed high capacity HP blade server waiting for a connection request.
In the automatic allocation mechanism, the host requesting for connection details is provided with a permanent connection details (including permanent IP address), hence, once the address is given out, it is totally removed from DHCP address pool, therefore no device will ever use such address. In the manual allocation, just like the name implies, DHCP only keeps track of IP addresses manually assigned to users in a network, hence, the DHCP maintains no address pool. In the dynamic allocation mechanism, the DHCP maintains an address pool and assigns addresses to requesting hosts.
These assigned addresses are "leased" which means that ownership of the connection details are for a period of time. Once this period elapses, the address automatically returns to the DHCP pool and is ready to be leased to another host, hence address reuse is highly maintained in dynamic allocation mechanism. When a device is actively using a leased connection detail, it sends a message to the DHCP server requesting for extension of lease time.
The major different between automatic allocation mechanism and the dynamic allocation mechanism is the the lease time. while the default lease time for dynamic allocation mechanism is 3600 seconds, the automatic allocation mechanism has an unlimited lease time. Dynamic allocation mechanism does not suit all environment, for example the web or file servers. These servers are mostly internet facing servers and needs to have address consistency, hence, automatic allocation and manual allocation is best suited for such situations.
DHCP Structure
DHCP structure is composed of the DHCP server, the DHCP client and the DHCP relay agents. During a DHCP operation, both the client and the server interact using series of DHCP packet/message. A DHCP client is any network capable device connected to a network and has been preconfigured to make requests to connection information like the DNS, gateway and its own IP address. The DHCP header contains an option field which is used for storing tagged data containing DHCP control information.
The DHCP server on the other hand is also a network capable device containing a predefined ranges of IP addresses called IP pool and other network configuration parameters meant for other network devices. These information contained within the DHCP server is automatically given out upon a "valid" request from another network device (the host). Some configuration parameters are always constant and these include, the gateway, the primary and secondary domain name system while the IP addresses are maintained in a pool and can change depending on the configuration.

[DHCP relays are used when both the server and the client are not in the same network. Credit: Wikimedia. A creative commons license. Author: Yangliy]
Many a time, when you walk into a large organization and you are given a Wi-Fi access, the DHCP that currently served you the connection configuration parameter you just used to access the network might not be sitting within the same network as you. The DHCP relay agents are used to remotely provide DHCP services to client out side the network of a DHCP. Many reason could lead to adopting DHCP relay option and this could be for centralized network maintenance and or for network security purposes.
For remote connection purposes, the DHCP servers communicates to within the network system using user datagram protocol (UDP) port 76. Also the DHCP client communicates within the network system using user datagram protocol port 68.
DHCP Process
The DHCP process is the procedure in which both the DHCP client and server undertake for requesting and obtaining connection details. The DHCP process is summarized into four basic steps:
DHCP discover
When a network capable device first comes up within a network, it first seeks for an IP address. The DHCP discover message or packet is a broadcast message addressed to every host in a network, including the gateway, requesting for an IP address. Its more like waking up from a ten years sleep in the middle of the road and you're shouting for help about how you got there and where you are.
))
[A DHCP discover message is a broadcast from the client to the server using UDP port 68. Credit: Wikimedia. CC4.0 license. Author: Demchig0602]
Since this is not a normal network broadcast because it is addressed to a UDP source port 68 with a destination UDP port of 67. As already stated above, the client communicates using UDP port 68 while the host communicates using UDP port 67. No network communication is carried out without an IP address, hence, the client makes the DHCP discover message using a source IP address of 0.0.0.0 and a destination IP address of 255.255.255.255 which means all the users in the network.
With the Destination port number being 67 and destination IP address being 255.255.255.255, this forms a socket which will definitely be serviced by any DHCP server if it is active. A socket is a combination of an IP address and a port number.
DHCP offer
If a DHCP server is active in a network or a DHCP relay agent is present in a network, a DHCP discover message is responded with a DHCP offer message. Since the DHCP discover message is a broadcast, one might ask, what if there are multiple DHCP servers within a network? Well, the fastest DHCP gets to service the client with connection details. This is usually of a security concern, hence, DHCP is configured and some security issues addressed.
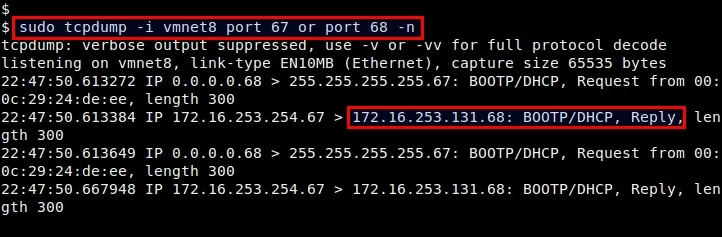
[A live DHCP packet capture showing a response from a DHCP server with a destination port number of 68 offering the client the IP address of 172.16.253.131 (highlighted in red). Credit: Flickr. CC by 2.0 license.]
The DHCP offer is also a broadcast form of communication, this is because the requesting client does not have an address yet. Also as expected, the DHCP server makes this offer using UDP port 67 and address it to UDP port 68, which is used by clients within the network. The DHCP server also includes the IP address it intend giving the client in the DHCP offer message and this message is address to all the client in the network using the IP address 255.255.255.255. This forms a valid connection socket.
DHCP request
Network communications usually takes an interesting turn. When a client gets a response from an active DHCP in the form of a DHCP offer, it does not just go ahead and starts using the address. Moreover, the only component of the DHCP offer just as stated above is the intended IP address for the requesting client.
The DHCP request message is also a broadcast message using the same UDP port 68 and destined for UDP port 67. Also the source IP address is 0.0.0.0 with destination IP address still 255.255.255.255 this is because the DHCP request message from a client to server is telling the server, which it still don't know its address, hence the use of broadcast address, "I will use the IP address offered in the DHCP offer message".
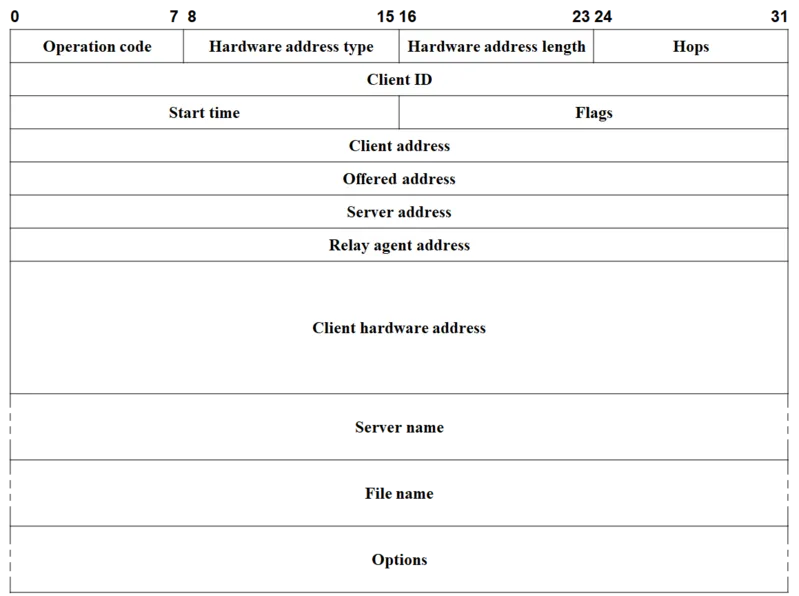
[A DHCP header showing different fields used by each DHCP operation. Credit: Wikimedia. CC4.0 license. Author: MichelBakni]
The DHCP request message apart from telling the active server that it is okay with the IP address it offered it, is also very crucial in the case where there are multiple DHCP servers in the network. This is because the DHCP request message also prevents other servers from making further DHCP offer. Broadcasts are not good within a network because part of the network resources are utilized in this form of communication and when a broadcast is sent out of a network, every client must process it.
DHCP acknowledgement
Just as the name implies, the DHCP acknowledgement message is used to affirm that the client accepts the IP address it offered in the offer message. This is also a broadcast form of communication with the destination IP address being 255.255.255.255 (broadcast address) and the source IP address being the server's IP address. Also the source port is UDP port 67 while the destination port is UDP port 68.

[summary of DHCP messages and operations. Credit: Wikimedia. Creative Commons Attribution-Share Alike 3.0 Unported, 2.5 Generic, 2.0 Generic and 1.0 Generic license. Author: Svkeulen]
Contained in the DHCP acknowledgement message is the remaining connection parameters for the client. This includes the default gateway, the subnet mask (hence activating the IP address for the client), DNS server address and also the length of time these connection details will last with the client. This is necessary since it will educate the client when to renew the lease in case where it is still actively using the address.
DHCP security vulnerabilities
As stated above, most DHCP operations are broadcast communications which means they are sent out to anyone that could receive the messages. This is a very serious security concern as these messages can be intercepted and modified. Just as we have stated above that there could be multiple DHCP in a network, an unauthorized persons could add a DHCP server in the network, this server is known as Rogue DHCP server.
Rouge DHCP servers are servers belonging to hackers and has the ability of responding faster to a DHCP discover messages. Once it gets the attention of a client, it could provide wrong connection details which could possibly direct the unsuspecting user to totally a different network. Come to think of it, how many of us checks the IP address assigned to us when we connect to a hotspot or a Wi-Fi?
Another security vulnerability of DHCP is the rogue client. As stated above, the DHCP maintains a pool of addresses that it gives out to client. What if there exist a client that continually asks for addresses from the DHCP server until all the addresses in the pool is exhausted? Once a "bad guy" gets hold of all the possible addresses available to DHCP server, the hacker can build a topology of the network and could carry out funny stunts in the network.
Conclusion
The DHCP is a protocol we use on daily basis and it comes in handy when connecting to the internet. This is because most of the time, we the users of a network are ignorant of the internal structure of the network we use. Network administrators also configures DHCP since manual assignment of connection details could be very difficult to track and also time consuming.
REFERENCES
- Dynamic host configuration protocol -Wikipedia
- Understanding the Basic Operations of DHCP -netmanias
- DHCP messages -on-time
- DHCP Starvation attacks and DHCP spoofing attacks -omnisecu
If you write STEM (Science, Technology, Engineering, and Mathematics) related posts, consider joining #steemSTEM on steemit chat or discord here. If you are from Nigeria, you may want to include the #stemng tag in your post. You can visit this blog by @stemng for more details. You can also check this blog post by @steemstem here and this guidelines here for help on how to be a member of @steemstem. Please also check this blog post from @steemstem on proper use of images devoid of copyright issues here.

))