

Introduction: Digital and Crypto Asset Storage and the Security Problem
At the end of the day, the goals are simple; safety, accessibility and security.
most or all of the missing bitcoins were stolen straight out of the Mt. Gox hot wallet over time, beginning in late 2011
- A hot online wallet which is always online thereby being rendered greatly vulnerable to hacking and DoS(Denial of Service) attacks plus even loss as a result of the collapse of a company offering such service and the fact that hot wallets are always connected to the internet even when not in use further compounds the risk associated with them.
- Traditional cold storage which may offer some form of security but is not the perfect option for frequent accessibility as often needed by cryptocurrency users. Furthermore, such items like paper and USB keys are also susceptible to loss and damage.

Not Hot, Not Cold, Just Right Storage: Goldilock
Every once in a while, a new technology, an old problem, and a big idea turn into an innovation.
Goldiblock is revolutionizing cryptocurrency key custody and digital assets storage by combining the security inherently available in offline cold storage and the convenience and accessibility of online hot storage thereby giving digital assets and cryptocurrencies full acessibility from anywhere anytime while still guaranteeing ultimate security. Goldiblock is built upon three premises which are absolutely true. These are that;
- Customers need to access their online data only occassionaly and for short periods of time.
- Private data must be isolated, secured from physical contact and fully backed up and that personal and;
- Private data must also be readily accessible whenever needed.

The GoldilockMechanism of Proven Technology and Innovative Processes
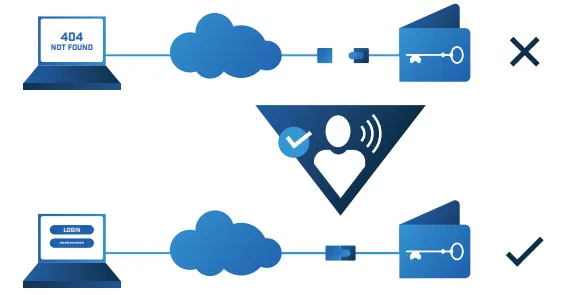
Great innovations that are ready to impact and provide new lasting solutions should really stand out from the rest. What is even more exciting about Goldiblock is that it employs technologies that are unique and offer a new and best key custody as well as sensitive digital data storage solution. These unique technologies include a physical airgap disconnection from electronic networks, scalable, physically segregated connectivity solutions, multisite encrypted data back-up, regressive conectivity and signal processing as well as biometric gateways.

Built Upon a Rock Solid Foundation: The NEO Smart Economy
- Compliance with Regulatory Measures: The operation of large institutions like big corporations and governments on the blockchain requires the ability to audit digital assets and transactions hence the need for such transactions to be known and verifiable. The NEO is committed to using Public Key Infrastructure standard for identity enabling it to issue and confirm digital identities hence the building of this mechanism into their ecosystem.
- A Superior Consensus Model: NEO combines the advantages of the Proof-of-Work consensus model and Proof-of-Stake as well as improvements in them to produce its own consensus algorithm called “Delegated Byzantine Fault Tolerance” (dBFT). It enables holders of tokens to be able to vote for delegates who must reach a consensus on acceptable transactions.
- Faster Transactions: NEO's Delegated Byzantine and fault tolerance consensus model renders obsolete the need for extensive mining by thousands of machines currently found in other blockchains and enables it to perform transactions at a blistering pace while keeping out transactional costs.

Exploring a World of Innovation: Into Goldilock's Unique Advantages.
For Users: Better Private Keys Custody
For users and consumers, Goldilock consists of layers of unbreachable security, an encrypted storage device stored in a vault which is itself in a secured data center. Data is kept offline most times when not in use thereby reducing susceptibility to hacks obtainable in hot online storages. Through the instrumentality of an authorized non-IP command through a Public Switched Telephony Network (PSTN), the storage device will be mounted remotely and become acessible to the user through a secure web login. Users can therefore acess their assets using encrypted channels to make any transaction they might want to make. After such a transaction, the device which is responsible for the secure management of private keys physically disconnects itself from the internet. This arrangement ultimately allows for top security for consumer keys while not sacrificing accessibility in the process.

Advantages for the Goldilock backed Institution.
Cryptocurrency exchanges aside, tons of institutions and corporations exist who continually deal with highly sensitive digital data. Therefore the need for data security runs accross virtually all decentralized transactions on the blockchain through traditional internet environments obtainable in the storage of personal credit information, health records and bank account information. Goldilock offers solutions to them all. Such solutions as applicable to various institutions would be discussed hereunder;
(a) Improvements for Cryptocurrency Exchanges
Centralized cryptocurrency exchanges organized in accordance with the current available technologies most times act as key custodians of private keys as well as crypto assets, while this may provide for some little convenience they are highly susceptible to hacks. Only in the last five years, hacks of exchanges has had devastating effects on crypto and users. Therefore, instead of storing cryptocurrencies in online hot wallets or leaving them virtually inacessible in cold storages, Goldilock, enables exchanges to be online when demanded which reduces transaction times, enables for better handling of high traffic during peak periods and above all, render cryptocurrency exchanges completely breachless.(b) Security for Online and Hot Wallet Operators
Goldilock's remotely automated airgap custody solution can be adopted by online hot wallet operators in order to improve upon the security of their systems. Goldilock will however, have no access to client data, relying on encrypted information flows routed through individual Goldilock user devices.
(c) Accessibility for Hardware and Cold Wallet Operators
Cold wallet operators can enhance their existing technology by integrating Goldilock to enhance their accessibility while still remaining remote and totally secure.
(d) Providing Priceless Conveniences for other Digital Asset and Storage Institutions.
Developments evolve society from one state of organisation of affairs to the other and therefore from one form of limitation to entirely new problems. Storage of sensitive data is one such area which has seen development in terms of becoming digitized. Digitization of such sensitive data as health records and bank records has however brought new concerns of security for institutions like banks, health centers and other institutions with data management concerns.
Goldilock is therefore the perfect solution for an on demand accessible storage for these types of sensitive data. In partnerships with banks, health centers,credit agencies, insurers and even governments, Goldilock offers an entirely new storage solution that is completely accessible anywhere, anytime while also being securely secure.

Applications Encrusted In Gold: A look into Goldilock'sApplication Layer and Security Suite
Goldilock is leading the pack for the development of tomorrow's consumer and institutional applications that are highly optimized for trust and security. Goldilock's applications include;
(a) The Goldilock Cryptocurrency Wallet
Built by the Goldilock Core development team, the Goldilock wallet will allow storing and transacting NEO, GAS and other NEP-5 tokens effecively securing the NEO. The wallet will run in a browser over authenticated SSL. The wallet will also possess state of the art features like;
- Keys that will reside on a unique harware wallet cut off from the internet
- Being brought online through a non IP command and PIN or voice verification over a Public Switched Telephony Network.
- Upon closure, the wallet will be disconnected from the internet.
- Every wallet will have a unique URL and will require two factor authentification for transactions.
(b) Goldilock API Services
An API allows for the creation of applications which access the features of an operating system or other application. In this case that operating system is Goldilock. Still developed by the Core development team, Goldilock's API services will allow institutions that have its wallet solutions to leverage Goldilock's cutting edge, patent pending technologies to improve on their security. API services will also make it easier for institutions to create applications that ensure privacy and consent driven use of data. Importantly too, the Goldilock API would also be open to be embedded into non decentralized applications. The end result of all these, is absolute security of data. The Birth of a Security Standard: A New Beginning in Digital Assets Storage and Protection and What Mass Adoption Of Crypto Ever Waited For.
Though the blockchain is built to be safer and better, security challenges as seen in numerous hacks of exchanges and key thefts which have cost billions of dollars still haunt cryptocurrency and their mass adoption. An individual and even corporations might not feel too comfortable entering cryptospace or even investing much when their investments are not to the best of their knowledge, very secure.
The need for the protection of sensitive data is also being highly recognized as a necessity worldwide which has prompted strict regulations requiring highly advanced techniques for the protection of sensitive data. Institutions dealing in highly personal and sensitive data have therefore being cornered into spending so much on the security of their systems without a corresponding return in value for money spent.
Goldilock is therefore very much the most perfect security system yet available for institutions to securely manage sand protect sensitive data entrusted in their care.
Therefore, only and only when cryptocurrencies are totally safe and investments and transactions totally secured would cryptocurrencies finally get the mass adoption by institutions and even governments. The time though is finally here because Goldilock is here. Goldilock is therefore the pacesetter for security protocols that would hopefully in the nearest future become the ideal standard even for licensing of crypto exchanges and other processors of personal data.
The Birth of a Security Standard: A New Beginning in Digital Assets Storage and Protection and What Mass Adoption Of Crypto Ever Waited For.
Though the blockchain is built to be safer and better, security challenges as seen in numerous hacks of exchanges and key thefts which have cost billions of dollars still haunt cryptocurrency and their mass adoption. An individual and even corporations might not feel too comfortable entering cryptospace or even investing much when their investments are not to the best of their knowledge, very secure.
The need for the protection of sensitive data is also being highly recognized as a necessity worldwide which has prompted strict regulations requiring highly advanced techniques for the protection of sensitive data. Institutions dealing in highly personal and sensitive data have therefore being cornered into spending so much on the security of their systems without a corresponding return in value for money spent.
Goldilock is therefore very much the most perfect security system yet available for institutions to securely manage sand protect sensitive data entrusted in their care.
Therefore, only and only when cryptocurrencies are totally safe and investments and transactions totally secured would cryptocurrencies finally get the mass adoption by institutions and even governments. The time though is finally here because Goldilock is here. Goldilock is therefore the pacesetter for security protocols that would hopefully in the nearest future become the ideal standard even for licensing of crypto exchanges and other processors of personal data.

The Use Cases
The practical applications of an invention like Goldilock even on the blockchain and across traditional internet environments are entirely limitless considering our world has gone digital and Goldilock provides digital safety and security that is entirely and for all intents and purposes, truly breachless.
(a) Saved by Goldilock: The Exchange on the Brink of Collapse
Changify.com is was what you may call a fairly successful exchange in the entirely novel world of cryptocurrencies. It enables the few who are still interested in cryptocurrencies despite security challenges to exchange their cryptocurrencies for other ones or back into fiat. However Changify.com is uses a hot, always online wallet making it very susceptible to hacks. The first hack ran into millions of dollars which totally put off Changify.com, they however rallied around, payed millions of dollars that were lost back to customers and also put in more millions for "security". It seemed that solved the problem but that was never to be. Changify.com was hacked again and it was in a board meeting for the liquidation of the exchange that Bobby confidently stood up and said, "I know of a solution, it is Goldilock. Changify.com has employed Goldilock's patent-pending user controlled, airgap activated security solution for cryptocurrency key custody and it is now over the moon! Lets not forget, all thanks to Goldilock.
(b) Healthcare at its best: Welcome to Stanforder University Hospital
One of the strongest drawbacks to providing quality healthcare providers face in contemporary times is the inability to maintain privacy while being able to share data with other relevant stakeholders like laboratories, doctors and pharmacists. Stanforder University Hospital was just like any other healthcare center that was bound by these limitations. It is however no longer the story. With Goldilock, Stanforder has enabled the secure sharing of information by patients, their families and other healthcare providers while ensuring the protection of individual rights like never experienced before. The end result is crowded hallways in Stanforder arising from the knowledge by patients that their records are safe and the best healthcare will be given them.
(c) Ben who swore not to keep Crypto again. Alert!! He just went back on his word! Thanks to Goldilock.
It was 2011 and Ben who who was quite fascinated with Bitcoin's concept had got himself a thousand Bitcoins and kept them all in his Mt.Gox exchange wallet. Barely a month later, Mt.Gox was hacked and he lost all his Bitcoin, what even compounded his anguish was that Bitcoin had gained more than a 500% increase in value. So not only had Ben lost his Bitcoins, he also lost his interest in cryptocurrencies which understandably anyone would do. The news of Goldilock has however made him change his mind. For with Goldilock he is satisfied that no Mt.Gox would be played on him again. Ever! By providing security, Goldilock will surely encourage adoption of crypto even by individuals and the bigger corporations and governments too.
(d) Get a President that is the people's choice now! Go Goldilock!
Sounds pretty off from our discussion right? No not so off, the subject matter Gildilock is quite versatile in its application. So yes! Goldilock can ensure the people's mandate. During elections, maxhines are always on which puts them at great risks of being hacked and data stolen, manipulated or corrupted. If according to Goldilock's concept, those machines are totally disconnected from the internet while containing a vaulted encrypted node which stores all vote data, then election hacks would become mission impossible.
 The above use cases in no way represent an exhaustive list of Goldilock's applications. For in a digital world like ours where digitization and storage of data of utmost sensitivity online has become a norm, then few things can be more wished for than the kind of security which Goldilock provides. Traditional institutions like banks, insurance companies, healthcare centers as well as a host of many others all stand to gain from Goldilock. Cryptocurrency operators as well as the blockchain also always needed more security.
Therefore, secure offline storage of digital assets combined with a convenience of accessibility anytime, anywhere is truly priceless technology that can be leveraged by anything digital.
The above use cases in no way represent an exhaustive list of Goldilock's applications. For in a digital world like ours where digitization and storage of data of utmost sensitivity online has become a norm, then few things can be more wished for than the kind of security which Goldilock provides. Traditional institutions like banks, insurance companies, healthcare centers as well as a host of many others all stand to gain from Goldilock. Cryptocurrency operators as well as the blockchain also always needed more security.
Therefore, secure offline storage of digital assets combined with a convenience of accessibility anytime, anywhere is truly priceless technology that can be leveraged by anything digital.

The Goldilock Tokenomy of LOCK Tokens
Registered as a NEP-5 token on the NEO blockchain, the LOCK token would be the gateway to accessing all of Goldilock's services. The LOCK token when coupled with Goldilock's proprietary smart contract logic would also allow for the storage of cryptocurrency keys as well as other digital assets.
These audit entries will ensure that every time your private key is brought online, this access is written to immutable storage that can be queried from the Goldilock Wallet.The LOCK token would also enable Goldilock to provide users with records of their node activitywhile their data is kept completely private and secure. More information concerning token distribution can be found here

The Team
What immediately befell me when I read through the Goldilock whitepaper was a great reapect for the genuis, innovative team that has thought out the idea that is now called Goldilock. A look through their profiles and i was not disappointed either. The team boasts of well experienced professionals with more than a decade combined entrepreneural experience in financial services, emerging technology and marketing and innovation.
Tonny Hasek is co-founder while Jarod Epps is both co-founder and CEO.



The Goldilock Advisors

Goldilock Partners


Check out this video for a quick walkthrough;
Other information sources;
tweet: https://twitter.com/Blezd_ben01/status/1027147012330934273?s=09
goldilocktwitter









