
It's well known that most passwords are inherently insecure and that it's remarkably hard to create a password that is both highly secure and will pass most password checks.
A password like p@ssw0rd1! which sadly will pass most "secure password" checks, can be cracked within a few minutes simply by brute forcing with a dictionary attack.
What's worse is that a lot of sites store passwords in plaintext, weakly hashed or hashed with salt that is the same for all passwords.
That means if an attacker can get a dump of the database, say because the site is using wordpress or some other laughable security nightmare, then the attacker can brute force the password offline at their convenience and once they have just one password, then they have them all.
Long complicated passwords are difficult to remember.
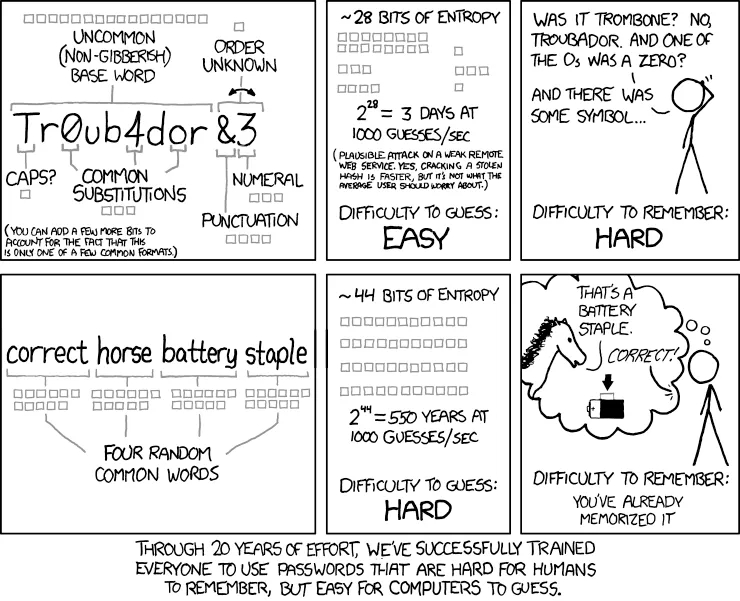
Even diceware style passwords like "correct horse battery staple", are difficult to remember and require writing down.
All of these systems create what is known as password fatigue.
People get tired of memorizing passwords to every site they need log into, so they choose passwords that are easy to remember and therefore weak.
A number of suboptimal solutions have emerged to deal with password fatigue, neither of which are real winners in my book.
The first is the "social media" login. With this solution, your favorite social media site authenticates you. They also get to know everything you're doing online in exchange for this privilege. Furthermore, if your social media account gets compromised, so does each and every other site you visit with those credentials. Truthfully, from a security perspective "social media" logins are worse than reusing the same password for each site you visit, since every site you authorize is listed right in the settings of your social media profile. Anyone who logs into your account can get into every other site you visit with no further trouble.
The second solution are password keepers. Plugins that reside in your browser. They can generate cryptographically strong passwords for each site you visit. But where do you think those passwords are being stored? For almost all of them, it's plaintext in your browser's cache with a "backup" kept "in the cloud".
That's how you can sync passwords between devices. Your browser just uploads all your passwords to some service, and that service has painted a huge target on it's back. It doesn't even have to be hackers. What happens when one of these services runs into financial troubles and has to lay off a bunch of employees? Your data is put on a thumb drive and sold to the highest bidder. More so if you're someone prominent.
You think many so called "hackers" are elite? That's not where these leaks come from. In almost every case it's been shown that someone on the inside has helped either willingly or inadvertently.
Keep in mind that in the business world, if you're not paying for it, you're the product being sold.
So we've established that it's basically impossible to keep secrets. If you can remember it, then it can easily be guessed. If you can't remember it then you're going to need help. Either social media, or passwords.txt file on your harddrive, etc. But is there maybe a better solution?
Maybe the problem isn't the method "i.e. diceware", but the list of words.
Specifically the emotional impact of those words, is what is making them hard to memorize.
Let me ask you something.
What's easier to remember?
music change chandelier tamborine
or
bloody piece of crap let me in!
Here's a fact.
A long list of random, disjoint words is going to be much harder to remember, than a fluent sentence comprised of an arbitrary number of emotionally impactful words.
This is the power of "Cryptography Using Slang and Scurrility In Numerical Generators" aka CUSSING.
We take the basic concept behind the diceware scheme (rolling dice and picking words from a list that matches 1 word to each possible combination of dice for n dice) and change up the list to a list comprised of common, easy to remember, emotionally impactful phrases.
In this case we're talking about combining 2 easy to remember phrases.
"bloody piece of crap" and "let me in".
This is generated from 2 rolls of 5 dice, just like normal diceware.
The difference here is that we replace single words with emotional, profane, even violent and ignorant speech.
Now, the real problem with any password scheme is entropy.
Entropy is the random bit of the equation and frankly it's importance cannot be overstated.
Entropy is what really secures any password and nothing contributes entropy to the universe like a long sustained explosion of expletives that would cause a sailor to blush and say "hey man calm down, there's truck drivers in here".
Imagine how this will work when voice printing becomes common place. It really is the ultimate password system.
In the spirit of such great RFCs such as RFC 2549 which describes a novel method of IP packet transmission using environmentally friendly methods.
I'd like to ask your support in adopting "Cryptography Using Slang and Scurrility In Numerical Generators" as a replacement for the current implementation of diceware as used in modern popular crypto wallets such as trezor.
This would provide one final layer of security, since if someone did have physical access to the device, who would believe if the device reported it's recovery seed as "bugger, off, drop, dead, jackass" etc?
The core of this improvement begins with finding a significantly long list of words and phrases that would qualify.
I'm thinking a solid list of "censored words" would be a good basis for this as it so happens I found one.
Now just drop one of these lists into the diceware word list of your favorite crypto wallet, recompile the software on your trezor or other wallet and make absolutely memorable passphrases that couldn't be hacked in a thousand years.
No foolin! This post is 100% Steem Powered!