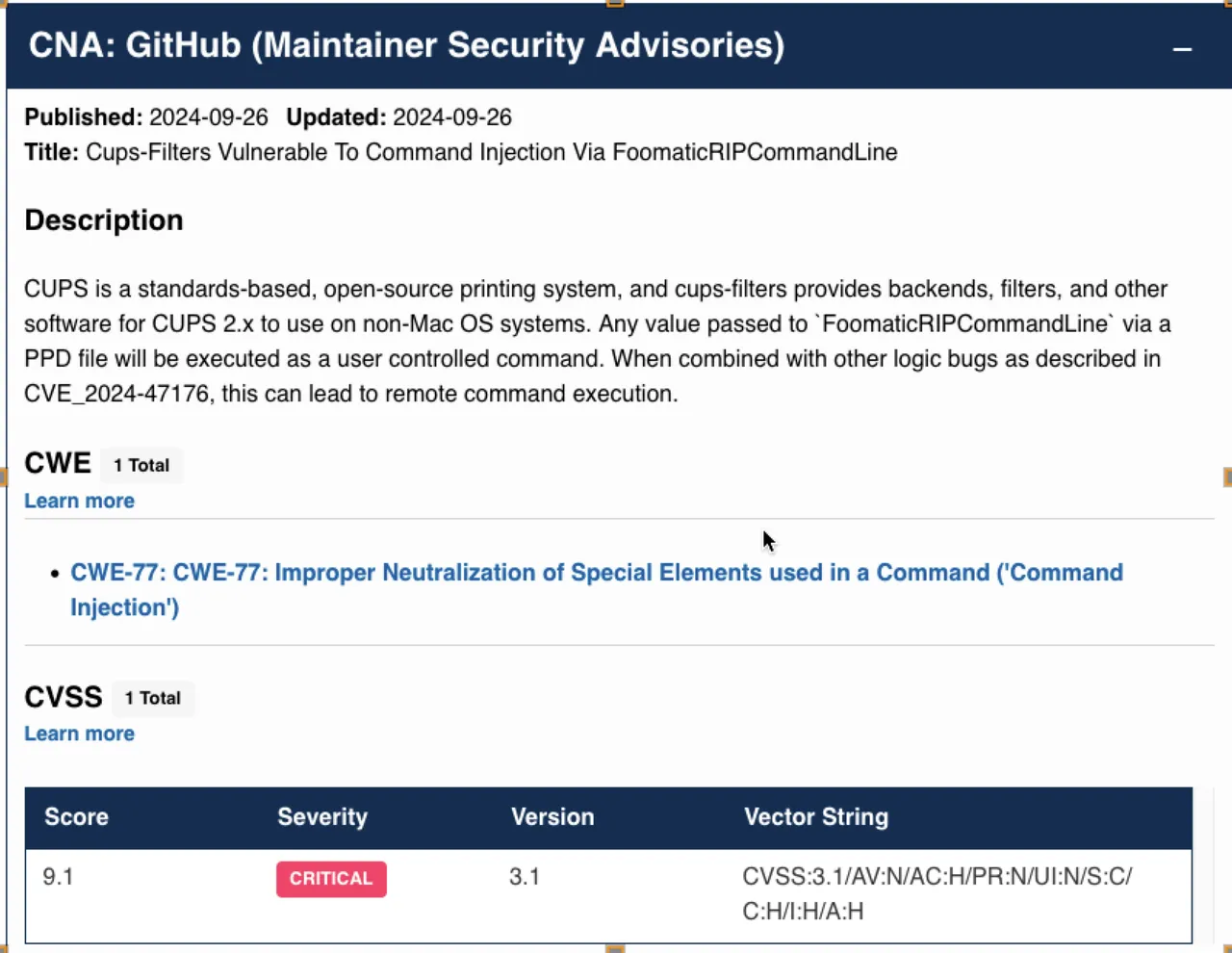
For the past few days a high severity vulnerability impacting multiple GNU/Linux distributions is going around and as expected, this is from the CUPS printing stack.
Details can be found here www.evilsocket.net
Steps for ensuring your Debian GNU/Linux is not impacted
Check for cups-browsed with: systemctl status cups-browsed
root@host:~# systemctl status cups-browsed`
cups-browsed.service
Loaded: not-found (Reason: No such file or directory)
Active: inactive (dead)
Lets scan the port sudo nmap localhost -p 631 --script cups-info
One scan gave a core dump:
root@host:~# sudo nmap localhost -p 631 --script cups-info
Starting Nmap 7.01 ( https://nmap.org ) at 2024-09-27 11:40 UTC
Stats: 0:00:00 elapsed; 0 hosts completed (0 up), 0 undergoing Script Pre-Scan
nmap: timing.cc:710: bool ScanProgressMeter::printStats(double, const timeval*): Assertion `ltime' failed.
Aborted (core dumped)
But the port itself is closed
Starting Nmap 7.01 ( https://nmap.org ) at 2024-09-27 11:45 UTC
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000054s latency).
PORT STATE SERVICE
631/tcp closed ipp
Inspect the installed packages:
apt list --installed | egrep '(cups-browsed|libcupsfilters|libppd|cups-filters|ipp)'
libcupsfilters1/xenial-infra-security,now 1.8.3-2ubuntu3.5+esm1 amd64 [installed,automatic]
Loo for cups related packages: apt list --installed | grep cups
libcups2/xenial-infra-security,now 2.1.3-4ubuntu0.11+esm7 amd64 [installed,automatic]
libcupsfilters1/xenial-infra-security,now 1.8.3-2ubuntu3.5+esm1 amd64 [installed,automatic]
libcupsimage2/xenial-infra-security,now 2.1.3-4ubuntu0.11+esm7 amd64 [installed]
Disable & remove the services:
If the printing and document management is not used on the server, delete the related packages as follows.
apt remove libcups2 libcupsfilters1 libcupsfilters1 libcupsimage2
These steps will make sure that the usually high severity (9.1) rated vulnerabilities are removed from the servers.