
As more and more people starts using the Ledger Wallet, it became important to support any type of operation possible to broadcast on the Hive network. People often use L2 solutions like dapps and games (f.e. Splinterlands) utilizing the custom_json operation. It was possible to sign transactions with custom_json from the very beginning but due to ledger devices hardware limits (RAM mostly), it was not possible to sign all transactions.
The main limiting factor is RAM size on the ledger device. Most transactions fit easily into the limited space of ledger memory, but some transactions just don't. An example transaction that could not be signed with a ledger device is this one:
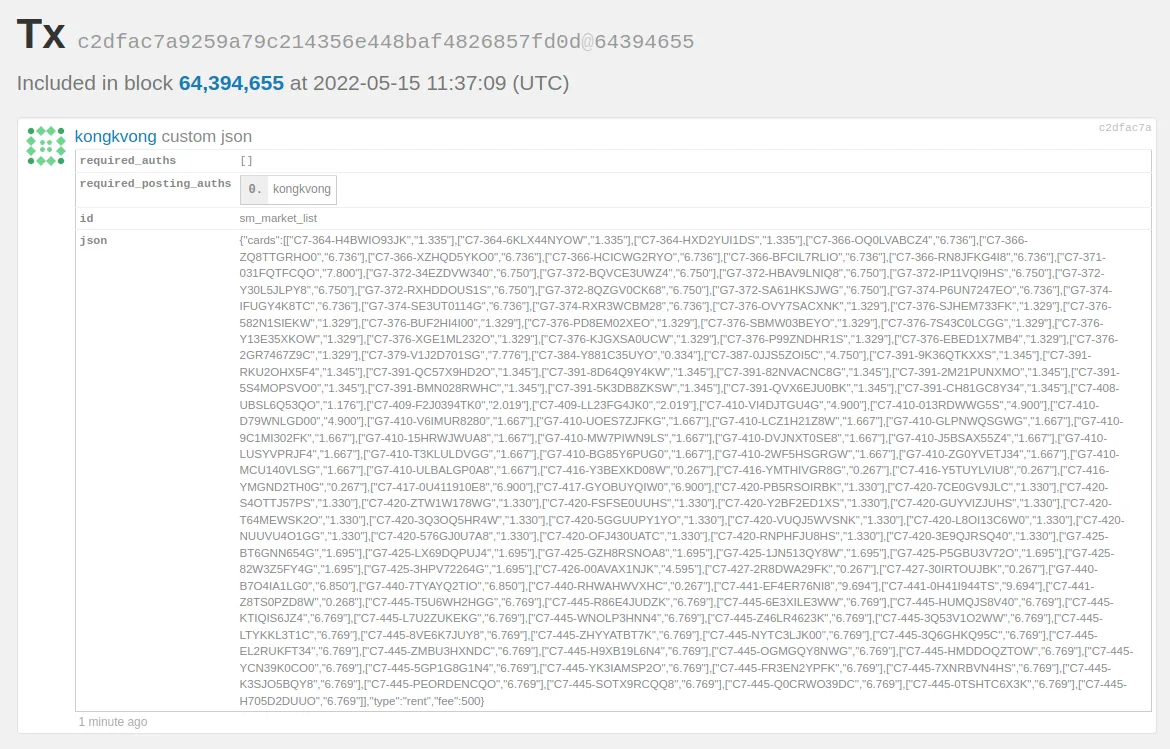
As you can see, it contains quite a big json field that could not be parsed on the ledger and displayed to the user. It's just not possible.
Blind signing as a solution to sign anything
This is a known problem for other blockchain and ledger applications. The solution for this problem is quite easy: blind signing in which the user does not see parsed transaction but rather the digest of the transaction. The digest is a hex string representation of the serialized transaction. Example hash looks like this: B2BF27F105D0E0E12F8BC913C8E124B2138E711AFAEAA7E85F186C2D8387F446.
Blind signing is the ultimate solution to sign any type of operation and even multiple operations at once.

But if it's so good, why do we even bother to use any other approach? It's because blind signing poses a risk to the user. It is not possible to convert digest back into the transaction, hence it's not possible to tell what transaction/operation you're accepting on your device. It is a matter of trust that the wallet developers do not fake the digest sent to the device.
Blind signing as an attack vector
An example attack vector could be like this: scam wallets show a valid transaction to the user but the fake digest, pretends to be the digest of the valid operation. The digest could be created from the transfer transaction (i.e HIVE or HBD transfer from the victim to the attacker).
So the user, while thinking he's signing the game-related transaction, in fact, is signing the transfer operation which ends up losing the assets.
Blind signing disabled by default
To mitigate the risk, blind signing on your device is disabled by default. If any wallet tries to use the feature it will receive an error message and the user will see the warning on the screen. It's impossible to use the feature without the user's knowledge.

You have to manually visit application settings and enable it.

Users should take special care when signing hashes. It would be beneficial to create open-source, publicly accessible tool that could calculate the transaction digest. This could give the user another level of confidence that he's signing a proper transaction.
Wallet developers should consider hash signing as a fallback of the normal process and use it only in case of the transaction is too large to sign in a normal way.
Hive Ledger Wallet
It will be possible to sign any transaction on Hive Ledger Wallet pretty soon. This will be a significant improvement for people willing to protect their accounts with the Ledger device.
I'm waiting for the new feature to be merged and rolled out in Ledger Live for existing users. Meanwhile, I updated the javascript library that is used to communicate with ledger devices as well as the CLI.
The library got two new methods:
async signHash(digest: string, path: string): Promise<string>
async getSettings(): Promise<Settings>
interface Settings {
/**
* Determines if hash signing is enabled.
* */
hashSignPolicy: boolean
}
The CLI got a new option to blindly sign supported operations. I will also add a new mechanism that could be used to sign any transaction from the file.
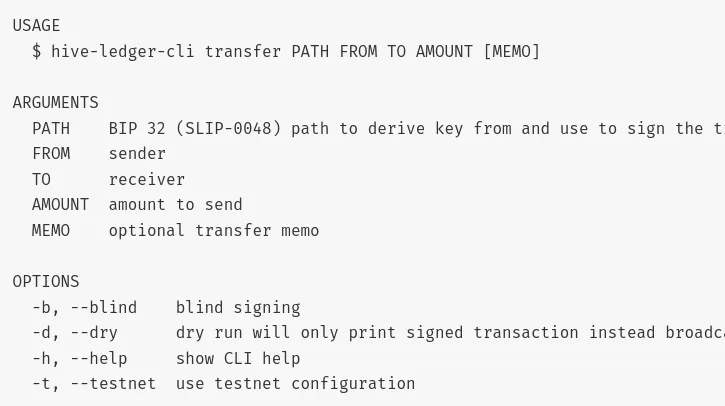
Stay safe, and enjoy using Ledger wallet with your Hive account!.
Don't forget to support me with your witness vote! Click on the image below:
