Do you know what HTTPS means?
How it is different to HTTP?
Do you care?
In all honesty, you don't have to understand how it works, but you should definitely care what it does. The aim of this article is to give an overview of the benefits of HTTPS and why you, a user of the glorious world wide web, should take it seriously. We'll skip all the technical jargon too, however, at the bottom of the article, you'll find some links to further reading if you want to learn more.
Tip: If you don't know what HTTP or HTTPS means, fear not. HTTP is just an acronym for the conversational framework used by computers to talk to each other when serving up your favourite websites. The S in HTTPS stands for Secure.
This article was inspired by some of the of the conversations I've seen lately around HTTP vs HTTPS for the APIs that Block Producers are providing, which you as an EOS token holder will use to interact with the blockchain. The arguments generally boil down to one of these:
- I've got nothing to hide.
- Everything on the blockchain is public.
- It's too expensive and difficult..
I argue that none of these arguments are relevant, in general or in the context of the EOS blockchain. The bottom line is that it's not about hiding what you're doing, it's about making sure that no one can interfere with what you are doing.
HTTPS is basically a shield around the data that travels between your computer and another computer, preventing prying eyes from looking at what you're sending. More importantly, HTTPS prevents someone from tampering with what you’re sending. This is the kicker. As with most things in the world of tech, HTTPS is not a silver bullet that solves all of our security woes. It's still possible for someone to tamper with your data, but with HTTPS it requires a lot more effort. Security is all about increasing the cost of an attack to the point where it's not feasible. In most situations, if someone wants something bad enough, they'll find a way to get it. Certain law enforcement agencies and hackers have been incredibly creative in their approach, usually involving a healthy dose of social engineering (getting someone to do something for you).
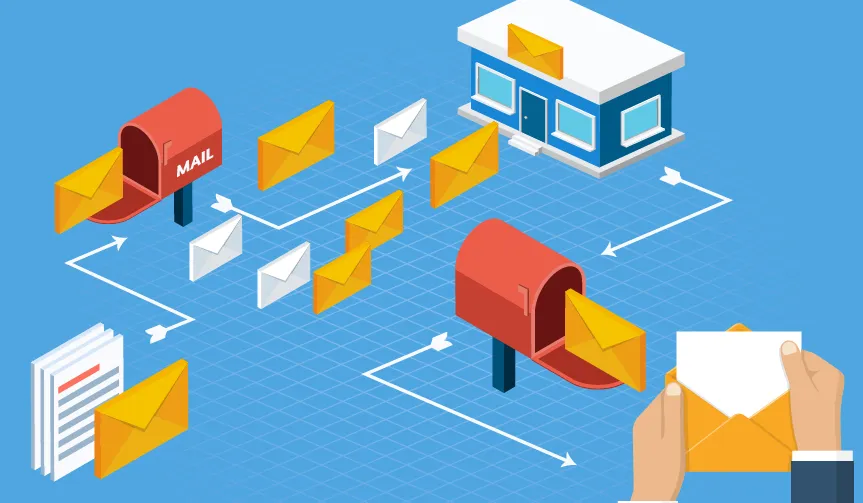
When you're browsing the internet, data doesn't generally flow directly between you and the website you're browsing. It has to make a few stops along the way, passing through other servers as it does so before being forwarded on. A great analogy for this would be the postal system. When you send a letter, it will go to a local post office where it's sorted and forwarded on. This continues until the letter reaches a distribution centre near to you, where your friendly mail service will deliver the letter to your door.
In this analogy, using HTTP is like sending a postcard through the postal system. The message is sitting there for the world to see. Now, those of you who agree with #1 above will declare, "I don't care who reads my message." That's fine and dandy, but it's irrelevant.
Well, what about #2? "All the information in the message is in the public domain anyway! There's nothing new in this message that can't be discovered on the blockchain." That's almost correct: being able to watch messages fly around allows you to attribute a message to the source a lot easier. This isn't an issue for most people, but if you're performing huge transactions from your home office, someone might be interested to know where that home office is located as it's more than likely your private keys are there too.
The most important fact that counters #1 and #2 is this: your postcard will be handed between a number of people, all of whom have the ability to read and modify the content of the message before it reaches you. Modify, change, edit. Let’s say that you send a postcard to your friend, asking them to send a payment to your bank account account '123456'. Your not-so-friendly mail courrier changes your message to include their account number, '654321' instead of yours. When your friend makes the payment, they will now be paying the wrong person so you won't receive your money. By the time you realise what's happened, your postman is off on holiday with his new fortune.
HTTPS, in a very gross oversimplification, would be the equivalent of putting the postcard in a lockbox to which only the recipient has the key. And any responses from the server would arrive to you in a lockbox that only you can open. Now, a powerful law enforcement agency could take a shot at trying to get in there and maybe succeed, but unless you're a modern day Pablo Escobar trying to run your smuggling operations on blockchain, you're probably safe.
Ok, so enough of the postal system analogies, how does this impact me in real life? Well, have you ever been in a restaurant or store that offers free WiFi? The kind of WiFi that has no password and either lets you straight on, or asks you to click an 'OK' button? Anyone else who is connected to that network is able to see the traffic that flows from your computer to the WiFi router. If that person can then put themselves between yourself and the router, they have the ability to modify the data that you send and receive. For instance, they could replace all account numbers you receive with their own.
Even if you're using the best offline wallet on the market and the strongest passwords and a polarising filter on your screen, someone can swoop in and divert your transactions right under your nose.
What about #3? It's too expensive and difficult? Well, until a few years ago, this point would have some legs. SSL used to be pricey and tricky to configure, but this is 2018, SSL is free and virtually automated thanks to LetsEncrypt.org. But to be fair, if you’re running a block- producing node, you should be able to put an SSL certificate on your API!
At EOS Dublin, we firmly believe that block producers are the custodians of the EOS blockchain. It is our duty to do all that we can to protect the community from the bad guys. By ensuring that we provide secure, reliable channels of communication, we're reducing the chances of something going wrong. We can't ever eliminate it 100%, but we'll do our damned hardest to! In 99.9% of situations, there is no excuse not to use HTTPS.
Of course, this is only the first step in protecting yourself online. Next steps would be to look in to using a VPN service, but that’s out of the context of this article.
I promised some further reading, so here you go:
https://odetocode.com/Articles/741.aspx
https://www.digicert.com/TimeTravel/math.htm
https://blog.cryptographyengineering.com/2013/12/03/how-does-nsa-break-ssl/
https://hackernoon.com/a-technical-deep-dive-on-meltdown-and-does-it-work-5c395579b2a1