
Why use Tor?
Classic travelers do not provide complete anonymity, even if we navigate using their anonymous features.
If we want to be active on the Internet with absolute anonymity and we do not want to know what we are doing while we are on the internet then the answer is in the Tor network.
I2P
Invisible Internet Project or I2P is an anonymous network whose purpose is to protect communications from third party monitoring.
Used to send messages using pseudonyms, and anonymous browsing and chatting. Its other applications are writing a blog and transferring files away from prying eyes.
The technique used by I2P to achieve the anonymity of its users is based on the garlic routing process, corresponding to the onion routing used by Tor.

If we want to use I2P, all we have to do is go to the page and download it. There we will find any information we want to install and use.
Freenet
Freenet is a free software that allows us to share files anonymously, browse, chat on forums without fear of censorship, and publish "freesites".
Freenet users are part of the network offering their connection, and a part of their hard drive for file storage.
Communications and files being trafficked to Freenet are encrypted and transported over multiple nodes to make it more difficult to determine the content and the final recipient.

Due to encryption, the user can not find out what is in the reserved disk space.
Although the individual user is not responsible for the content that hosts on that particular computer section, this may be dangerous.
The use of Freenet directly implies the acceptance of the above, because whatever the user does within it, he relies on his reserved space.
Unlike Tor, which allows anonymous web access as well as anonymous servers, Freenet is a standalone network.
Through this network, we can not connect to services like Google or Facebook, because it is not a proxy server.
Because Freenet is a distributed storage space, everything that goes up there remains anonymous and secure. We would say it looks like the Las Vegas networks.

Another difference between Freenet and Tor is "Darknet" or "Friend to Friend". By using this feature, we connect with the software that our friends run on their computer. This provides greater security and increased resistance to attacks.
What can I find on the Dark Web?
The Dark Web, as we have said, is a subset of the Deep Web, and we have already outlined several of the benefits that the way it works.
At this point we will see what is hidden in the dark rooms of Dark Web. There is nothing to be said to be scaring us, but to be the occasion to be more careful if we find ourselves in these parts of the Dark Web.
Botnet and electronic "fishing"
In the Dark Web one can find botnet, sets of online devices running automatic programs.

We have already seen one of Botnet's most well-known uses in the DDoS attack guide, but are also used to send Spam and malware propagation.
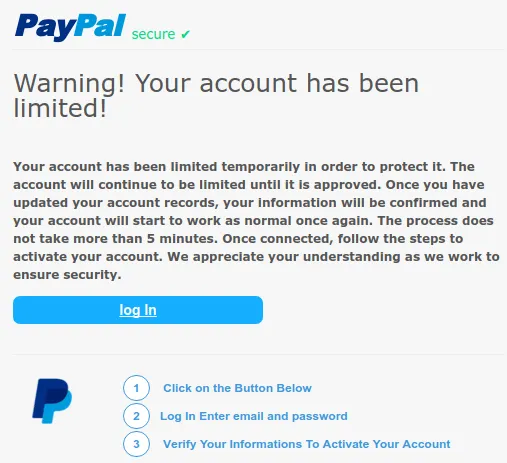
At the same time, the Dark Web contains many pages of "fishing" data and financial data of users.
Most of these are faithful copies of popular services such as PayPal. Their purpose is to trick unsuspecting users into filling in their real account details.
Dark Web Black Market
Dark Web black markets are trading in white flesh, trafficking drugs, weapons, and even military equipment.

Silk Road, the first modern black market
The Dark Web Beginning in Dark Web was made with Silk Road, created by Ross William Ulbricht.
The "Silk Road", as mentioned in Greek, started its operation in February 2011.
As part of the Dark Network, the page was hidden behind Tor's services, so the identity of its users was considered to be absolutely safe.
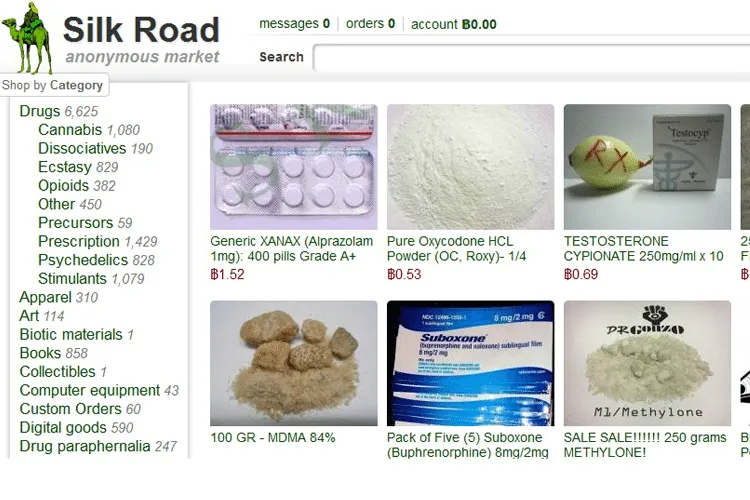
Buyers' registration on Silk Road was absolutely free. Sellers initially bought bills through auctions, and later paid a single amount.
In October 2013, the FBI closed the website, and Ross William Ulbricht was arrested as the founder of the page, nicknamed "Dread Pirate Roberts."
In November 2013, former site administrators opened Silk Road 2.0, which closed in November 2014 as part of Operation Onymous.

In February 2015 Ross William Ulbricht was charged with a total of eight accusations. He is currently serving a life sentence, without the possibility of a review.

Sheep Marketplace
A smaller black market in Dark Web was the Sheep Marketplace, which became more popular after Silk Road was closed.
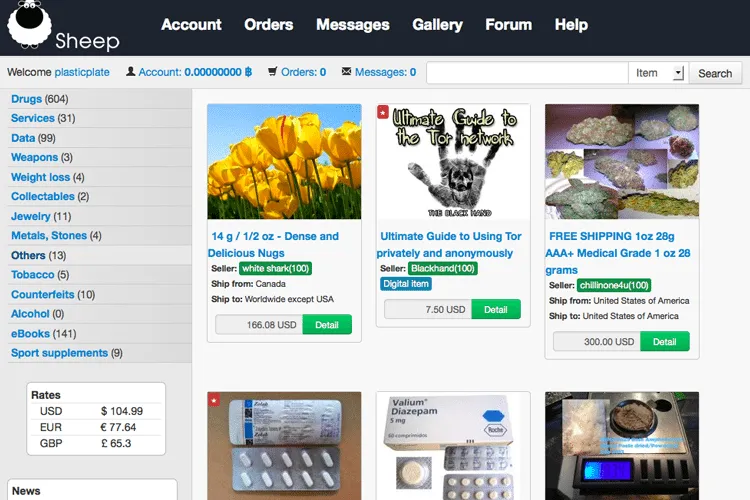
In December 2013, site administrators announced that one of the vendors involved in this site managed to steal 5400 Bitcoin from the users of the site.
Users were able to prove that the amount was up to 40000 Bitcoin, and days before theft, Bitcoin downloads were blocked from the site.

In March 2015, the Czech police arrested a man as a suspect for theft. The reason was the purchase of an expensive home using Bitcoin.
The case was closed in May 2016, as two men from Florida were traded through the Coinbase.

Illegal pornography
Black pornography is also a place of concern for the Dark Web. In Dark Web one can find pornographic material for every kind of taste.

Hackers
The Dark Web is definitely the paradise of hackers, who are paid in a harsh way to provide their services.
Dark Web hackers operate individually or in groups, and undertake various electronic crimes. It has also often helped to eliminate pedophilia circuits.

Bitcoin, Games, and Dark Web
Most Dark Web transactions are done using cryptocurrencies. The reason is because payment with a non-physical currency helps to maintain anonymity.

Many users are trading in digital coins, and then transferring these funds to games such as World Of Warcraft and Second Life.

Games of this kind provide the ability to convert their digital coins into real money.
Thus, users convert Bitcoin into a game currency, and then into a physical currency, which they withdraw to a bank account. This is a process that helps to launder money.
Terrorism
There are sites that claim to be used by ISIL and ISIS, including a fake seized by Operation Onymous.
Nobody knows whether and what are real or false, but there are, and they seem to be influential.

Following the Paris attacks in 2015, such a site was violated by the hacker group GhostSec, and was replaced by a Prozac ad.
Paid Assassins
These are pages where you can hire paid murderers. Prices depend on the person who is the target, ranging from a few thousand to tens of thousands of dollars.

Such pages can be found from cold performers, to torturers who will make their victim suffer until it dies.
Pink Meth
Pink Meth was a site that contains photos and videos of pre-teenage girls, to older women.
Users are paid to upload their former material. Many publish personal information, such as names, addresses, and profiles on Facebook.
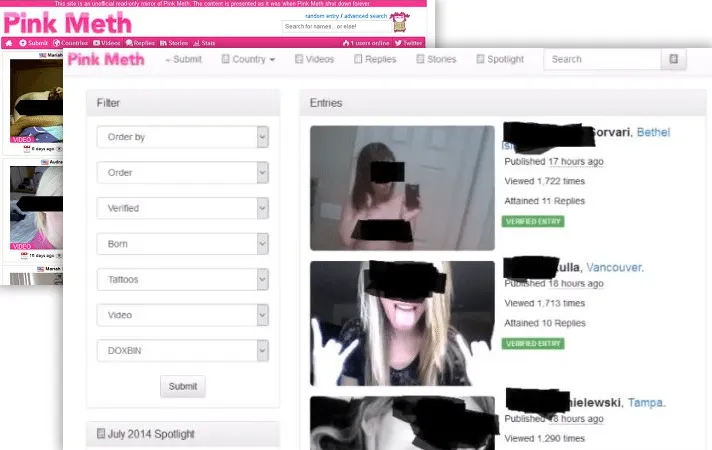
It has been reported that the page was closed by the FBI, but rumors say it has reopened deep into the Dark Web.
Human experiments
Another type of site you find in Dark Web is the one that promotes organizations that engage in tumultuous experiments on living people.
The most shocking piece is the exact descriptions of the experiments. Whether it's true or false, the descriptions of the experiments are creepy, and the images that accompany them even more.

Deep Web Documentary
Deep Web has been so much involved in the past few years in the world of technology and the law that some have been interested in making a documentary about it.

The documentary is a production by Alex Winter, Marc Schiller, and Glen Zipper, directed by the first. It was rolled out in 2015, and its official screening took place on 21 November of the same year on the EPIX network.
Production covers events on Silk Road, Bitcoin, and Dark Web policy. At the same time, he is following the trial of Ross Ulbricht, founder of the "Silk Road".

It is a good source of knowledge and pleasant to follow. If we want to know more about Dark Web and the Silk Road, then it's definitely worth giving it a chance.
Myths about the levels of the internet
At the beginning of the article we analyzed the two real levels of the internet. But there are theories that want the Internet to have more layers.
Theories range from arbitrarily certain levels that do not have any real reason to exist, up to levels deep into the waters of science fiction, based on technologies that just do not exist at this time.
Bergie Web
One of these levels is supposed to be the Bergie Web, which is said to be the last dam before the dark waters of the internet.
This level supposedly consists of "underground" websites, such as 4chan, Freehive, 1eden, Black Hat World, and Bittorrent.

Of course, the above pages are open to everyone, and appear on search engines, and it is easy for everyone to create and download torrent.
Because they are supposed to deserve their own level, no one knows. However, we have not found any serious source that refers to this level.
Marianas Web
The Marianas Web is supposed to be beyond the Deep Web. Its name is said to come from the most well-known point of the oceans, called the Marian's Tomb.
As long as the real trench is down, the nonsense that sounds for the Marianas Web is ten times more submerged.

It is assumed that this level contains the world's greatest secrets, but access to it is only possible using quantum computers.
Quantum computers are a real concept, and various companies around the world, including Google, are working to develop them.
However, they are at such an early stage of development that the claim that an entire network allows access only through quantum computers simply comes from everywhere.
It's just as if someone claimed in 1903 that there was a base on the moon that you needed a spacecraft to visit when the Wright Brothers were still experimenting with seconds on the first planes.
The levels of paranoia
References covering the latest levels of the internet demonstrate how unflattering these theories are. It seems to be a reflection of the imagination of a paranoid mind, and nothing else.
So, there's a legend about a level that is the hacker's war zone, because they seem to have had nothing better to do.

The next level is empty, because ... so. Maybe they want to do AirBNB?
The last and deepest level is the reward of whoever wins the hacker war, and whoever has this level will control the entire internet.

Do not know what is more sad, that some have devised such nonsense, or that many ignorants believe them, without thinking that they have no logic?
Instead of choice
Before letting you swim in the deep waters, we would like to give you a summary of all this information.

- Deep Web is not the same as Dark Web, but the second is the subset of the first.
- Dark Web is not the most dangerous place to find but it needs attention.
- Within the Dark Web, anonymity is our own responsibility alone.
- A good browser that provides a great deal of anonymity is Tor. Especially if used in conjunction with a VPN.

- With I2P we will have the same anonymity, perhaps even greater, just the road is more difficult.
- To create a small secure and anonymous network, we can use Freenet.
- There is in no way any form of network that requires access only to a quantum computer. In the future we could theoretically exist, but let's first have fully functional quantum computers, and we see.
Deep Web #1: https://steemit.com/blog/@andrewclk/andrewclk-or-deep-web-1
Dark Web #2: https://steemit.com/blog/@andrewclk/what-is-dark-web-2
Dark Web #3: https://steemit.com/blog/@andrewclk/what-is-dark-web-how-to-access-and-its-safe-3
Follow me for more: @andrewclk
Twitter: https://twitter.com/ishere_andrew